- May 12, 2020
- 3
- 0
- 0
So to start,
I'm not the typical "my girlfriends watching me" security hackz0r post.
I'm no expert or even close but I do have a general idea of what and how an Android should run.
I detected the device was playing up, slowing down, screen looking blurry. Odd icons in notification tray. But before I go into the things that I don't have data for.
What I do have data for and would appreciate input on is the following.
S20 Ultra Exy
Less than two weeks old
Cloned apps
Adjust system settings
Apps being given permissions and even admin rights.
I have tried to make sense of logs but it appears that the attacker is using a mixture of Dex, Java, Bluetooth and Odin in some remote access capability.
I have tried factory resets and the cloned apps which have been given there own emulated storage that I can't touch on the device.
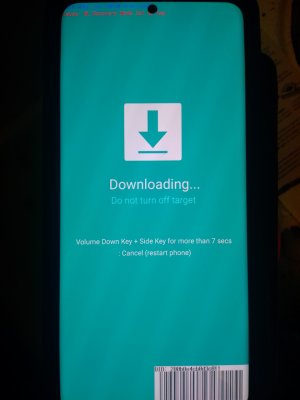
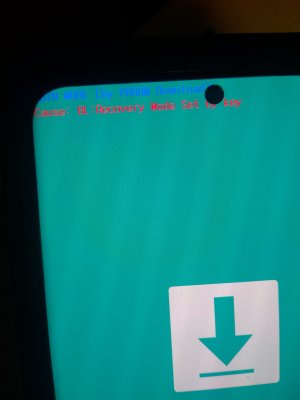
An unlocked Odin Bootloader! (see pic) that's when I knew I needed more advice. From what I know once the Bootloader has tripped Knox and secure folder won't work.. SECURE folder appears to work..
Ive had apps go into desktop mode randomly..
Look I don't want to sound like that crazy tin foil hat guy, but It is becoming a trend in my trade. I've just listed some of the easily proved things.
I've uploaded logs and screens to the cloud and able to share with anyone who knows this stuff well.
Basically I've got an $1400 phone security marvel that appears to have been Bootloaded and maybe rooted remotely.
I have my suspicions at the office and I would like to try and trace the attackers location.
To be clear this device is no way associated with the infected.
That Bootloader was accessed just by going into the preload process I was planning on trying to wipe the cache and then saw it the Bootloading option and realised this is pretty serious...
I'm not the typical "my girlfriends watching me" security hackz0r post.
I'm no expert or even close but I do have a general idea of what and how an Android should run.
I detected the device was playing up, slowing down, screen looking blurry. Odd icons in notification tray. But before I go into the things that I don't have data for.
What I do have data for and would appreciate input on is the following.
S20 Ultra Exy
Less than two weeks old
Cloned apps
Adjust system settings
Apps being given permissions and even admin rights.
I have tried to make sense of logs but it appears that the attacker is using a mixture of Dex, Java, Bluetooth and Odin in some remote access capability.
I have tried factory resets and the cloned apps which have been given there own emulated storage that I can't touch on the device.
An unlocked Odin Bootloader! (see pic) that's when I knew I needed more advice. From what I know once the Bootloader has tripped Knox and secure folder won't work.. SECURE folder appears to work..
Ive had apps go into desktop mode randomly..
Look I don't want to sound like that crazy tin foil hat guy, but It is becoming a trend in my trade. I've just listed some of the easily proved things.
I've uploaded logs and screens to the cloud and able to share with anyone who knows this stuff well.
Basically I've got an $1400 phone security marvel that appears to have been Bootloaded and maybe rooted remotely.
I have my suspicions at the office and I would like to try and trace the attackers location.
To be clear this device is no way associated with the infected.
That Bootloader was accessed just by going into the preload process I was planning on trying to wipe the cache and then saw it the Bootloading option and realised this is pretty serious...